How many of you know that the top websites like Facebook and Wikipedia use PHP? Of course, that might have surprised you. Why only PHP? Well, PHP is fast, dynamic, open-source and cost-effective. Besides, none of the website companies would ever want hackers to attack them. Thus, security is the topmost priority and every company is on a constant lookout for the best PHP web development techniques. So, what are the top seven development techniques that any custom PHP web development company must follow? How will these PHP development techniques reduce the risk of an attack? Let’s have a detailed look.

PHP Vulnerability trends over time
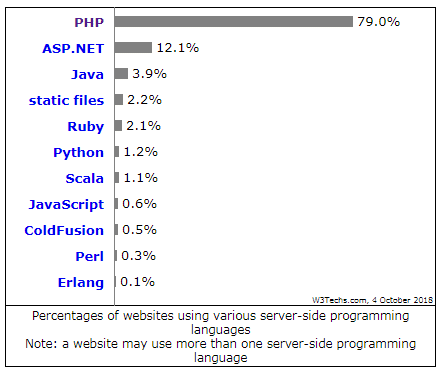
PHP might be getting old-fashioned with new popular scripting languages like Python in trend. But, do you know that PHP is the only server-side programming language used by 79.0% of all the websites? ASP.NET which is at the second place after PHP is only used by a mere 12.1% of the websites.
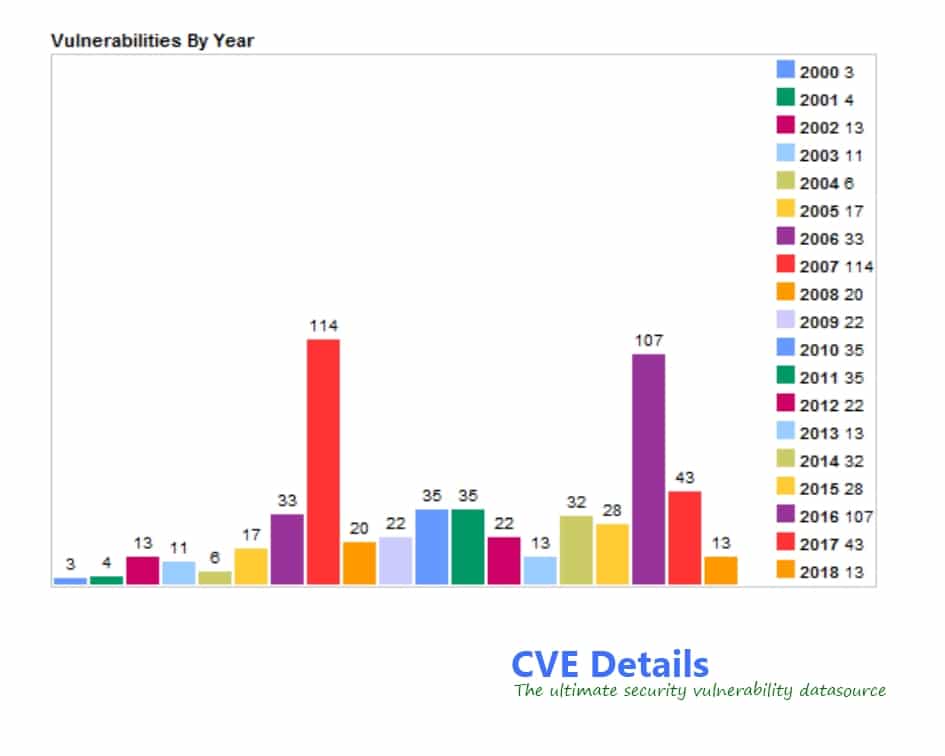
Now let us have a look at the vulnerability trends by year and type.
According to CVEDetails, security vulnerabilities like Remote Code Execution, Authentication Bypass, Denial of Service and Buffer Overflow have always been high in numbers. Also, from 2016 to 2018, the number of vulnerabilities have reduced. But, we can’t say that it is cent percent safe to deal with PHP websites.
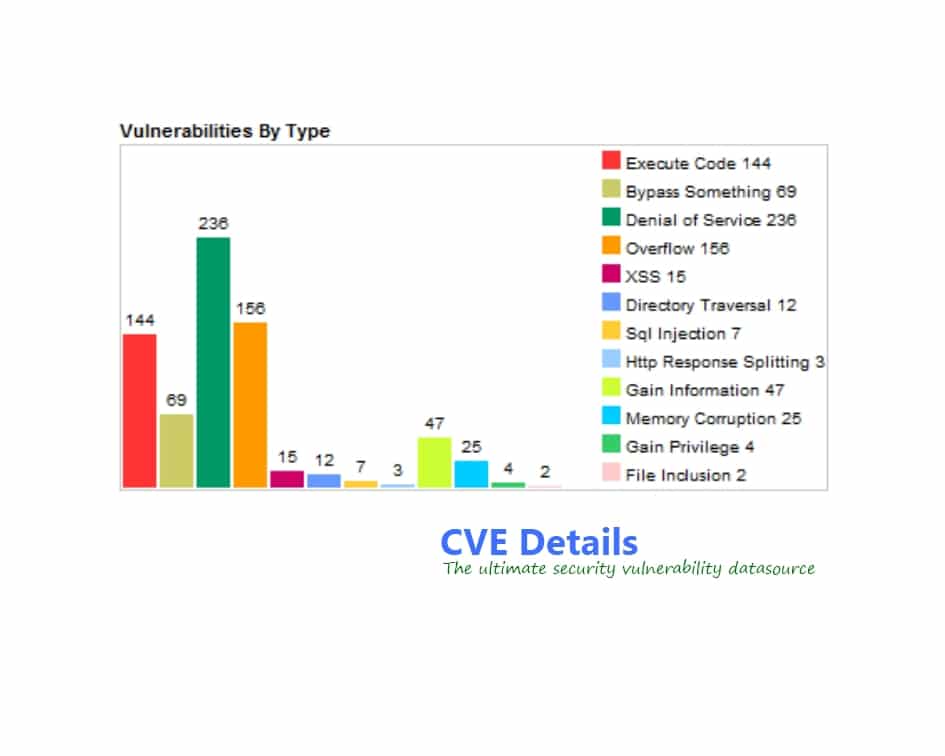
In fact, any top PHP development company would not want to compromise on its security. Developers will always want to prevent their websites from potential attacks. So, what are the most common security vulnerabilities in PHP? Keep reading to know more.
Most common vulnerabilities in PHP web development
How are hackers targeting the most vulnerable points of websites? Well, most of the attacks occur through SQL injection, Bypass Authentication, Remote file inclusion, and Remote Code Execution.
Let us have a complete look at these.
Remote Code Execution (RCE)
What happens if a hacker succeeds in uploading a code to your website and execute it? That is when a Remote Code Execution or RCE attack occurs. An attacker can even get full access to your website by instructing websites to generate files carrying harmful codes.
Bypassing Authentication
PHP programmers must make sure that every visitor doesn’t have the same privileges to their website. Sometimes they might validate a visitor with a wrong access level. For instance, the “is_admin()” makes some developers believe that the user is an admin. But, visitors are only allowed to view an admin page and they don’t have the privileges of an actual administrator. As a result, non-admin users may have access to features that only admins could reach.
SQL Injection (SQLi)
An SQLi or SQL Injection attack can happen when hackers send and execute their own harmful instructions to others database. And often everyone blames the PHP developers for such attacks. If developers don’t check the input from visitors for malicious code in advance, it can pass into the database.
PHP web development techniques to defend against security vulnerabilities
How can any PHP application development company avoid an attack? Let us know about some efficient methods to defend against the security vulnerabilities in PHP websites.
Foreign Access Restriction
How can you restrict any foreign access? One way is to manage the data files and scripting pages in a proper manner. Moreover, you can also redirect pathways by adopting new configuration files. For instance, in httpd.conf files, you can use the below-mentioned script.
<Files ~ ‘’.inc$’’>
Order allow, deny
</Files>
PHP Developers must also test their code during PHP web development as hackers can create a duplicated link to get privileged access. Through the admin’s data and password, hackers can get access to sensitive data.
Input Data Validation
You should never trust your visitors with their inputs. This is because even though you have developed your website with good intent, some users will always try to attack with wrong inputs. So, whenever you are designing an application, protect it against bad inputs. Using a filter to validate incoming data can help in keeping your application secure. Also, some users may turn off the JavaScript in their browsers and the validation of such users might not happen.
Moreover, PHP developers must consider all the types of input data for validation. One must check string contents and programming length of code with time for perfect validation. Sometimes specific scripts for direct input into the statements can also prevent attacks. Let us look at a sample script.
If(!ctype_alnum($_GET[‘login’])) {echo ‘’Allow only A-Za-z0-9.’’;}
$If(!ctype_xdigit($_GET[‘color’])) {echo ‘’Allow only hexadecimal values.’’;}
Input validation security can prevent buffer overflow and injection attacks to a large extent.
Front-end Testing
Sometimes the front-end code can cause problems. It is not always the case that you will find vulnerabilities in the back-end. So, you must perform a front-end test too. Though front-end testing may take some time to run manually, software is available for this purpose. Such software can test for you in a quick and meticulous manner. Some front-end testing tools include Jasmine, Selenium, Browsera and Needle.
Unit testing
Unit testing is the best method to find vulnerabilities related to permission and restricted functionalities. You can test the certain functionality of code snippet allowing you to know if a functionality is working or not. Proper unit testing is mandatory to check your application’s permission and restriction functionality.
Creating an effective framework
Sanitization and Form Handlers
Sanitization and Form Handlers are the best way to perform basic sanitization. For example, sanitization handlers work against variables and superglobals. They sanitize them before the problem gets to you. But, form handlers lead the data through some basic sanitization before allowing you to manipulate it. These handlers are more like security checkpoints. Sanitization handlers check for data while form handlers check forms.
Database Handler classes
If you want to identify and minimize any unnoticed security liabilities, develop a database handler class. Developers can also use custom PHP web development techniques like developing a database handler class for passing the incoming data through a sanitization handler. Let us have a look at a sample of database handler class.
class DbHandler
{
// Define database information like host, username, password and database name
// Define DSN(Data Source Name) for PDO(Php Data Object)
// Define Variables for handling the connection
// Methods of database handler class to connect, disconnect and execute queries
}
Testing code while developing it
It is always a good practice to test your code before finishing the entire code block. By doing so, you will be able to spot many of the vulnerabilities in your code in advance. You might not find these vulnerabilities if you had tested the code as a whole.
Consider a simple illustration for this. If you develop a method in a permissions class for account verification, testing the entire code in one go can be futile. Some bugs may get ignored and you may end up with a faulty conditional statement. On the other hand, if you had tested your code simultaneously while coding, you could have spotted those bad conditional statements.
Consistent coding methods
The most important practice of any PHP developer should be, being consistent with your code and methods. Yet, many of them make messy and erratic codes. The main problem with inconsistent codes is that they are difficult to work with. Also, inconsistent methods can lead to a confusing set of codes for the developer. This can cause many security issues too.
Let’s take a basic example. The most common forms of submission methods in PHP web development are the GET and POST. Even if the GET method is set to default, any hacker can interfere with the exposed query string part of the URL. So, PHP developers must avoid adding sensitive information to the GET pages. Besides, if you want to add any sensitive data to the web pages, the HTTP POST form submission method is better.
Signing off
Prevention is always better than cure. Attacks can lead to crashing of websites or even disclosure of sensitive information. Moreover, secure coding is very important to prevent losses. So, with these PHP web development techniques, you can protect yourself from any harmful users. However, if you want to be the best PHP development company, you must do anything and everything to keep your website safe from hackers.
Now, are you ready to apply these PHP web development techniques to stay away from those hackers?

